
On 18th July 2024, we hosted an online masterclass on how the attack surface is likely bigger than you thought.
You can see the full video below, but if you prefer text, then the following excerpts from the masterclass may be of interest. And remember, if your attack surface is keeping you awake at night, we offer a completely zero obligation initial assessment to help you understand where your biggest risks may lie. Simply fill out the form.
What Is the Attack Surface?
To begin, let's define what we mean by the attack surface.
In simple terms, the attack surface includes anything outwardly facing your organization that's connected to the Internet. Traditionally, this might mean IP addresses, open ports, and running software – but it extends much further.
Expanding the Definition
- External Controls: This includes social media posts, reviews on platforms like Trustpilot or Google, and any other online mentions of your company.
- Uncontrolled Information: Employee posts on social media, or data about your company available on other websites.
Here's a visual example. Imagine a business with the following:
- Computer Networks
- Staff Laptops
- Cloud Services Access
Every organization, regardless of size, will have some combination of these elements. Understanding this helps us know where to focus our cybersecurity efforts.
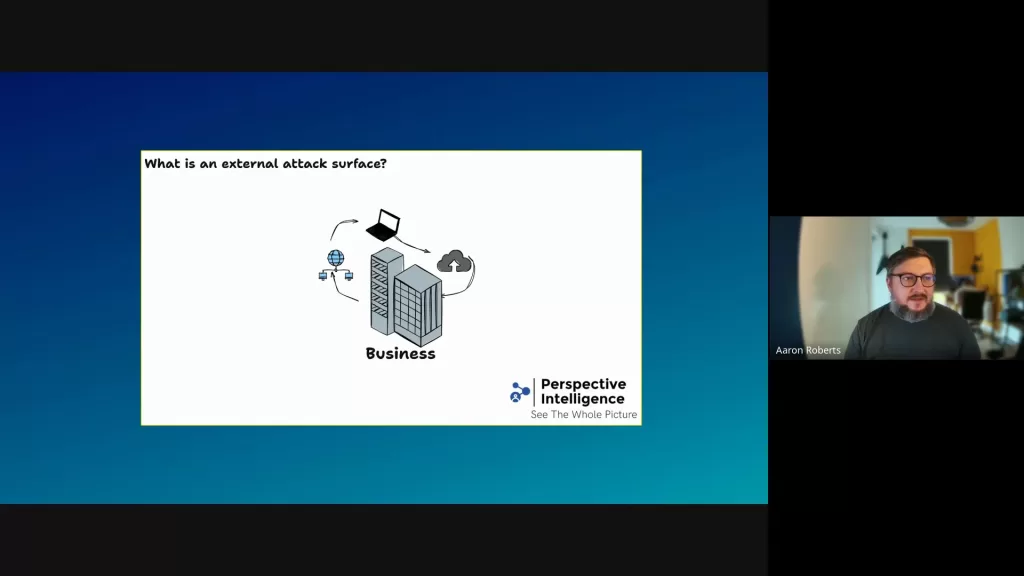
The Expanded Attack Surface
So, what should you be thinking about when considering the attack surface? Let's dive deeper into areas often overlooked.
Social Media
Employee posts on social media can unintentionally reveal sensitive information about your company. For example, posts on LinkedIn describing the technologies they work with can provide potential attackers with information about your tech stack. It's important to monitor and manage this kind of accidental data loss.
Sentiment Analysis
Monitoring social media sentiment around your company is critical. Negative comments can indicate potential risks or even attempts to manipulate your brand’s image. This isn't strictly a cybersecurity risk but still a threat to your business.
“We should be supporting the CEO, the board of directors, whoever's in charge to achieve business aims by ensuring that security policies and programs in place do the right job.”
Data Breaches
Data breaches present a significant risk, especially when they affect third-party services your company uses. Stolen user logins and personal details can be leveraged for malicious purposes, including blackmail or extortion.
Phishing and Brand Impersonation
Phishing attacks and brand impersonations remain significant threats, especially for larger companies. Fraudulent domains pretending to be legitimate can trick users into giving up sensitive information. Monitoring for unauthorized use of your brand imagery and taking appropriate action is crucial.
Deep and Dark Web
Awareness of the dark web is essential. Forums and marketplaces on platforms like Telegram and Discord where stolen data is bought, sold, and traded can contain your company’s sensitive information. Understanding how your data might appear in these places is key to strengthening your defenses.
Attack Surface Intelligence
Attack surface intelligence involves collecting data about your organization from external sources and assessing how this information could be used in an attack.
- Stolen or Breach Credentials: Looking for compromised credentials in data breaches.
- Vulnerable Software: Identifying and fixing software vulnerabilities.
- Accidental Data Loss: Monitoring social media for unintentional leaks.
- Brand Impersonation and Phishing Domains: Scanning for fraudulent activities.
The Role of Initial Access Brokers
Initial access brokers play a significant role in the current threat landscape. These are individuals or groups that gain access to an organization’s networks and sell that access to others, often ransomware groups.
Key Methods for Gaining Access:
- Phishing Emails: Well-crafted emails can trick users into divulging their credentials.
- Legitimate Credentials: Stolen or guessed credentials from data breaches.
- Exploitation of Perimeter Devices: Compromising VPN endpoints and other devices.
Real-World Examples
Here are some real-world illustrations of how initial access brokers operate.
Telegram: A 1.7 GB file containing logs was traded on Telegram. These files can be easily downloaded and contain valuable data such as usernames, passwords, and session cookies.
Russian Language Forums: Access to corporate networks as domain admins are sold for a few thousand dollars each.
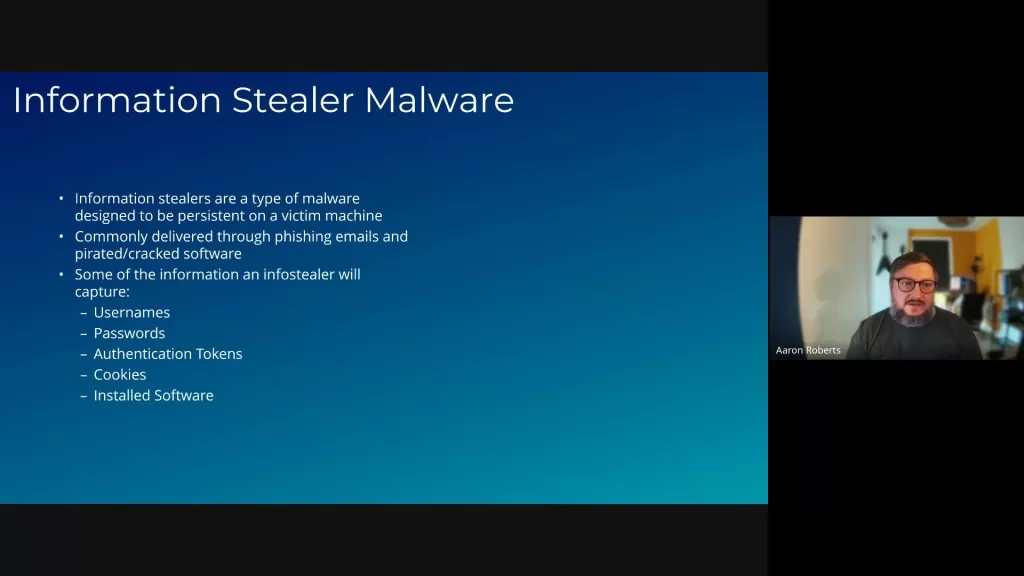
Information Stealers
Information stealers are particularly dangerous as they collect sensitive data from infected devices quickly and covertly.
- Persistent Malware: Designed to stay hidden and collect data over time.
- Types of Data Collected: Usernames, passwords, authentication tokens, session cookies, and more.
Here’s a peek into the information stealer market:
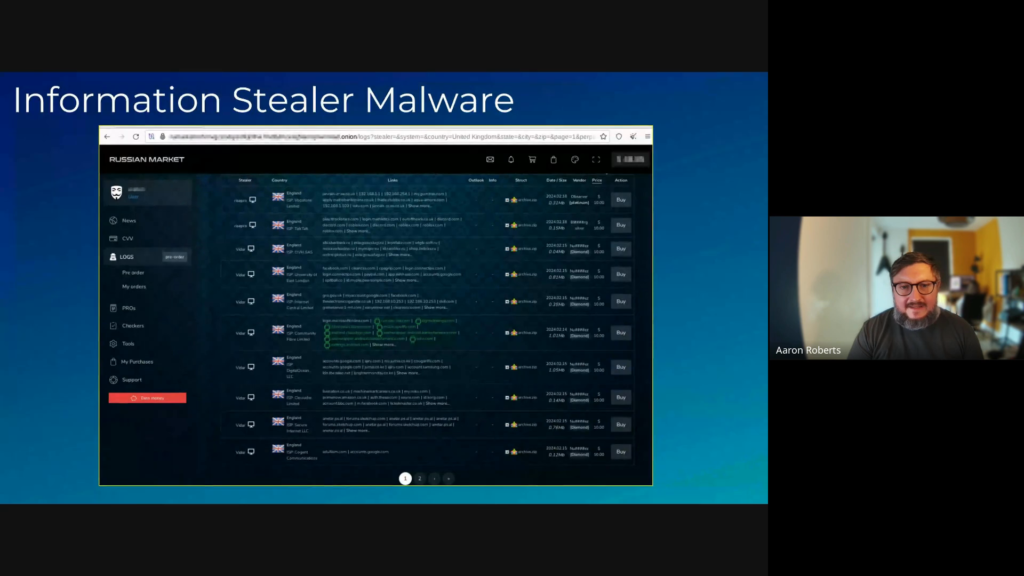
This data shows that information stealer logs are sold for as little as $10, making them accessible to almost anyone.
Further Considerations for Attack Surface Management
As we've discussed, managing the attack surface is complex, but some best practices can help.
Monitoring and Response
Implementing detection and mitigation plans is essential. Collect data, analyze it, and act on it. Here are some steps to get started:
- Invest in Security Services: Use managed services for ongoing monitoring.
- Block Browser Logins: Prevent employees from saving passwords in browsers and enforce the use of password managers.
- Leverage Open Source Tools: Tools like DNS Twist for detecting fraudulent domains and Spiderfoot for scanning are invaluable.
- Monitor Social Media: Use platforms for social media monitoring to track accidental data loss and sentiment.
Initial Security Steps
For smaller businesses, identifying where to start can be challenging. Key steps include:
- Understand Your Organization’s Critical Data: Know what data exists and what poses a risk.
- Invest in Necessary Tools: While the range of tools can be overwhelming, prioritizing the right ones is vital.
Aligning security measures with business goals ensures that security efforts support broader business objectives.
Conclusion
Understanding and managing your attack surface goes beyond traditional cybersecurity measures. It requires a comprehensive look at external threats, including those posed by social media, data breaches, phishing, and dark web activities.
If you'd like to assess your attack surface, we offer an initial no-obligation, zero-cost assessment of your external attack surface – complete with a human-written intelligence report.
Feel free to reach out at attacksurface.co.uk if you’re interested.
If you have any questions or need further assistance, don't hesitate to contact me on LinkedIn at @AaronCTI or on X (@AaronCTI).