
ThreatLens® is our bespoke, non-invasive, attack surface intelligence platform for both businesses and individuals.
Find critical cyber risks, verified by human analysts that automated solutions miss. Our 24/7 monitoring solution separates signal from noise and enables near real-time response to protect your reputation, backed with bespoke intelligence reports that focus on you. Every report is tailored to your current situation by our team of analysts. ThreatLens® gives you the ability to act decisively.

THREATLENS® FEATURES

Brand Misuse
Identify misuse of your brand whether it’s brand impersonation, phishing domains or concerted campaigns targeting your business.
Reporting
Every report we write is bespoke to you, get clarity and actions that actually help to protect your reputation instead of generic boilerplate advice that has no relevance to you.
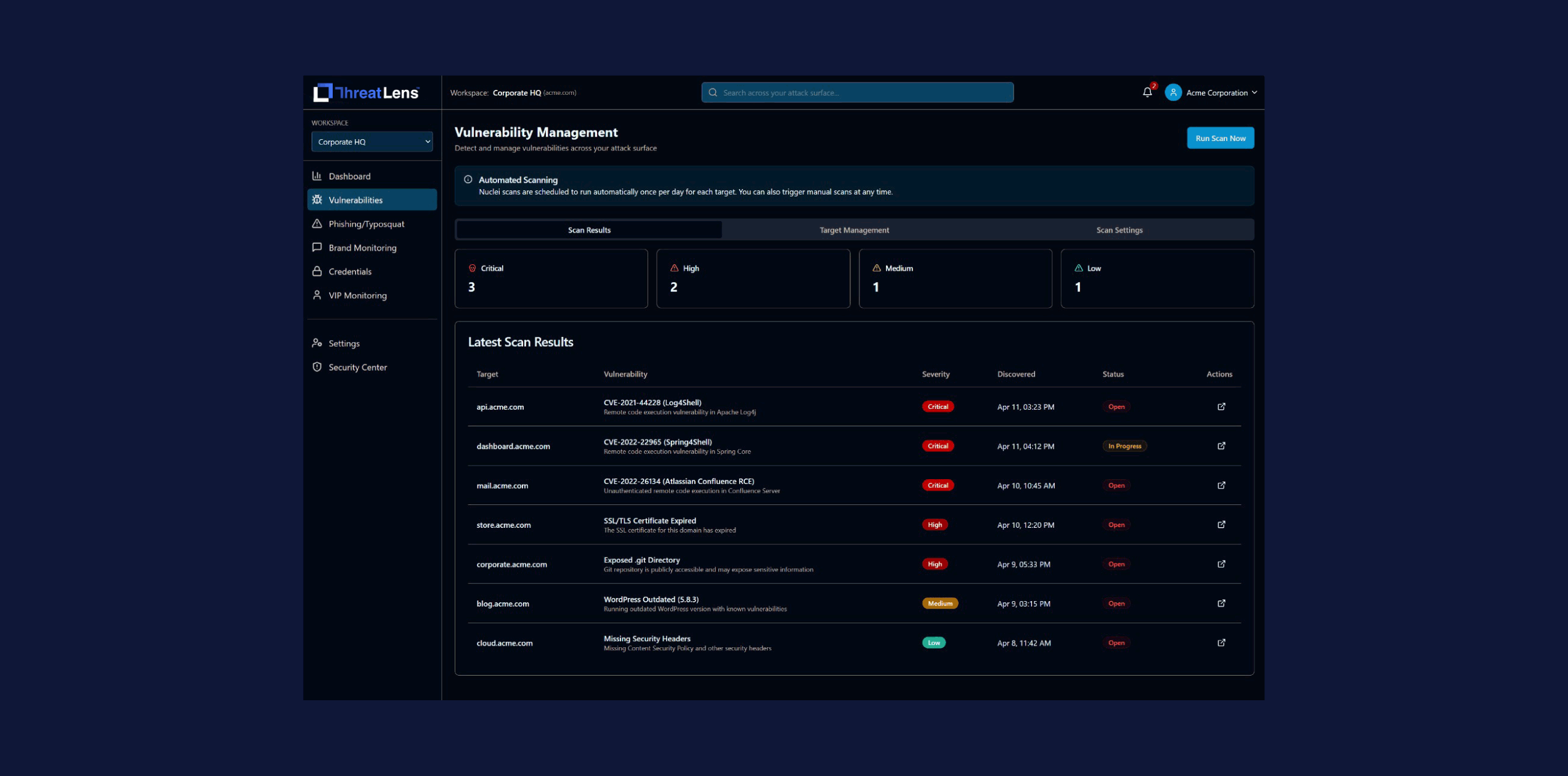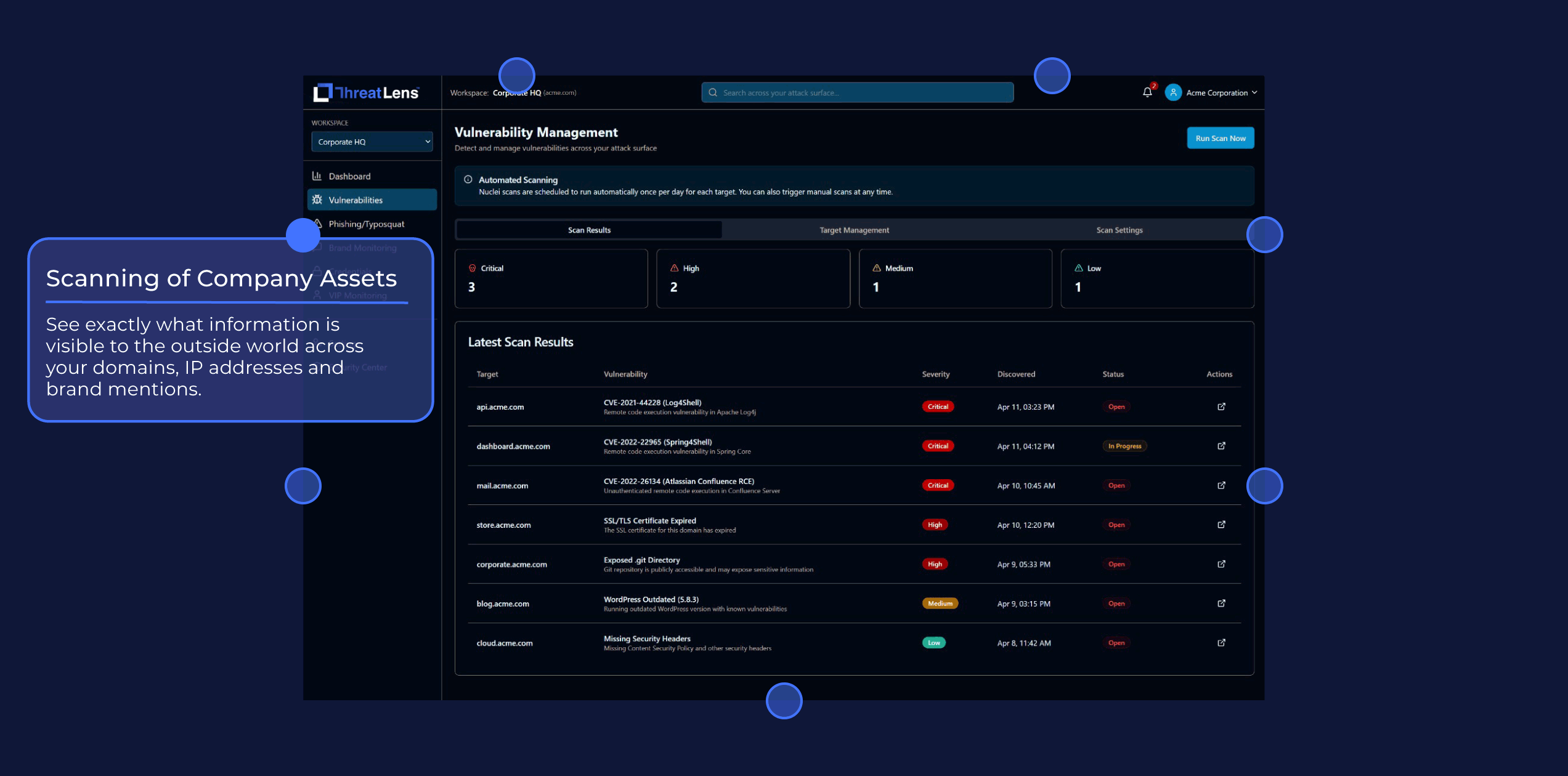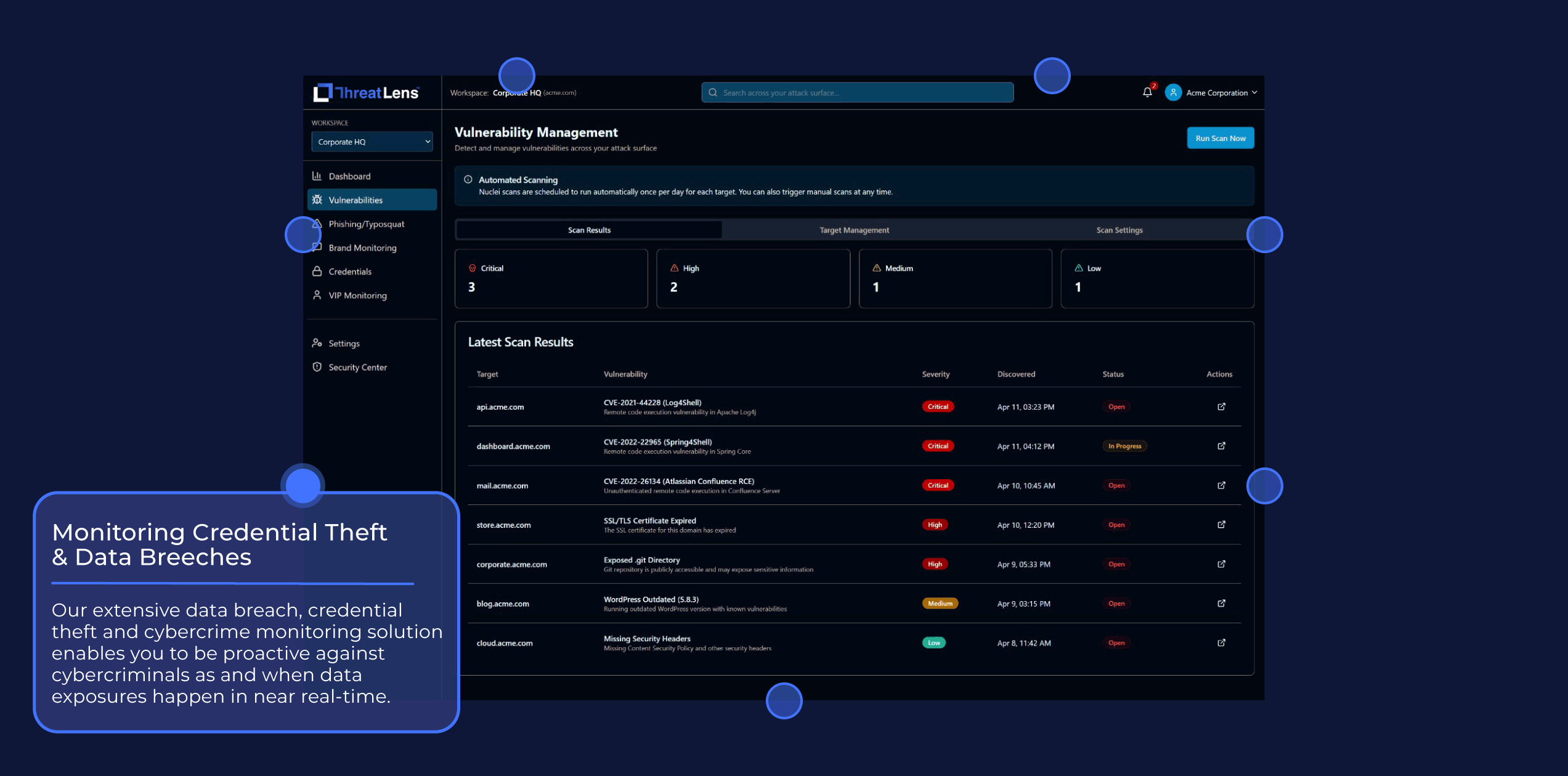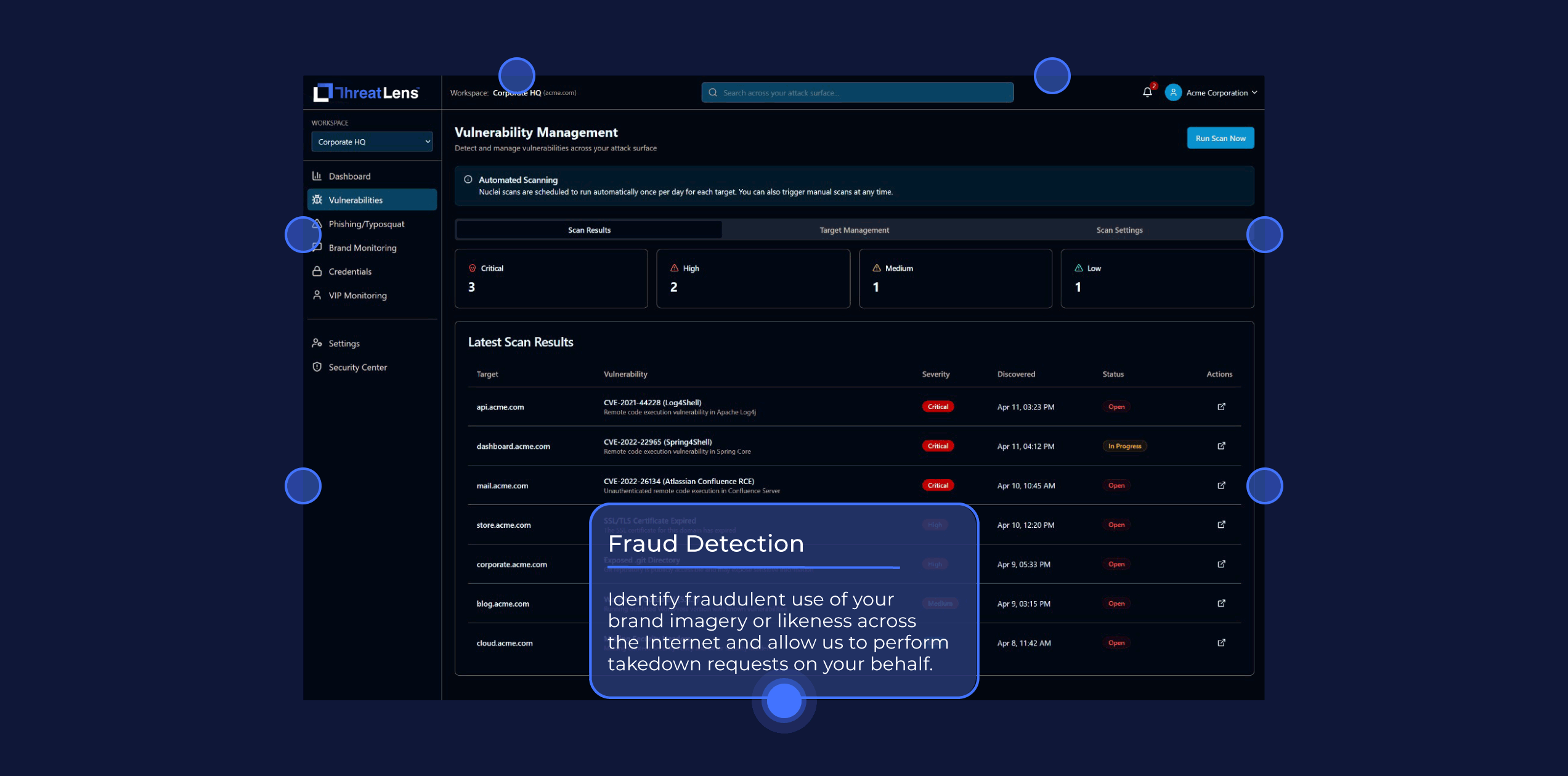
Scanning of Company Assets
See exactly what information is visible to the outside world across your domains, IP addresses and brand mentions.
Deep & Dark Web Monitoring
Stay on top of brand mentions across the cybercrime ecosystem across the deep and dark web. Be alerted when your company is referenced on a forum or messenger platform.
Monitoring Credential Theft & Data Breeches
Our extensive data breach, credential theft and cybercrime monitoring solution enables you to be proactive against cybercriminals as and when data exposures happen in near real-time.
VIP Monitoring
Protect your executives and VIPs with our full digital footprint assessments and monitoring services and reduce personal risk and reputational damage across social media, online mentions and our bespoke deepfake detection system.
Fraud Detection
Identify fraudulent use of your brand imagery or likeness across the Internet and allow us to perform takedown requests on your behalf.
A DEEPER UNDERSTANDING
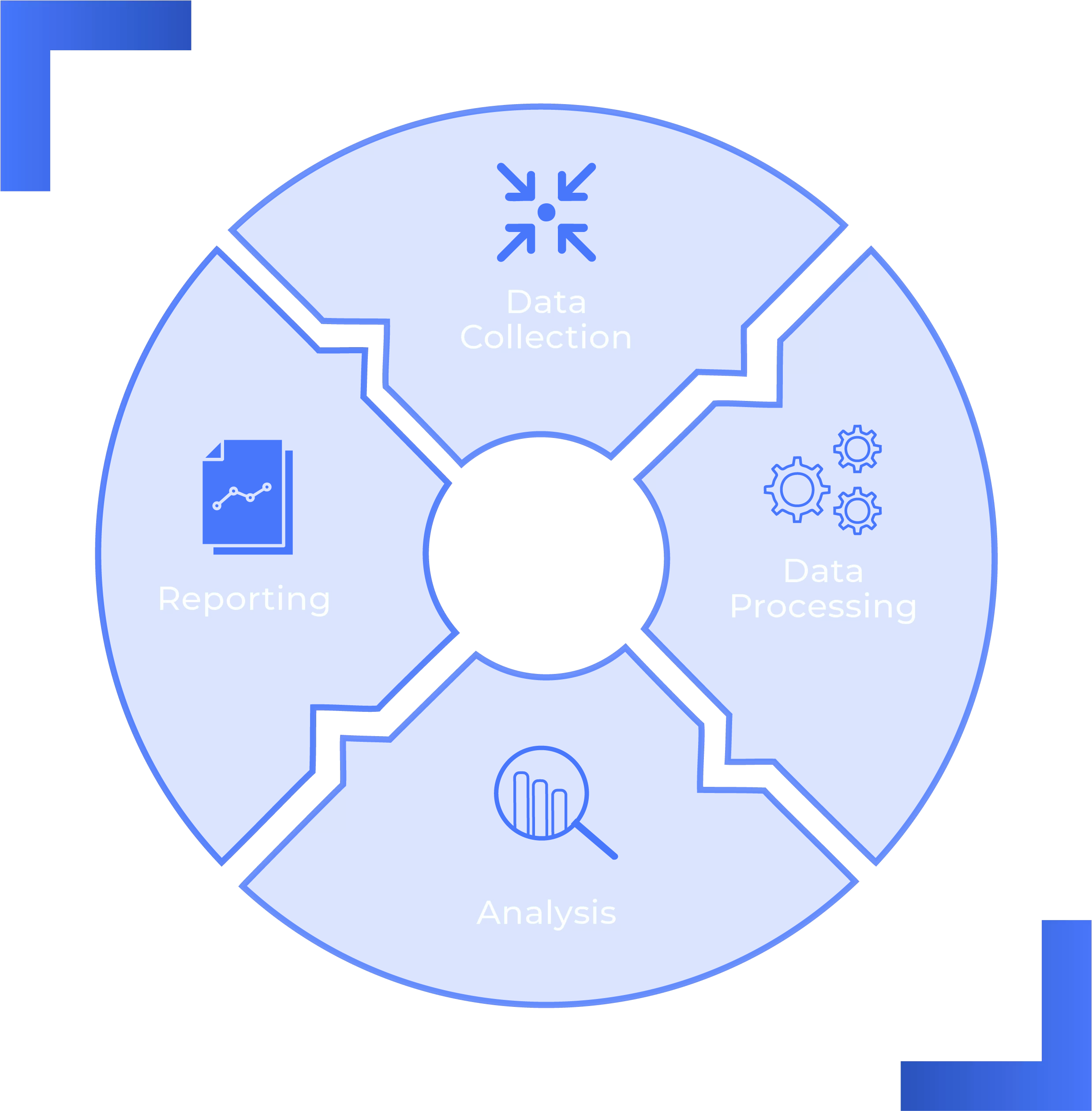
HOW DOES IT WORK?
ThreatLens® is a non-invasive, attack surface intelligence solution. We scour all corners of the Internet to find data about your business and your VIPs.
We collect this information, analyse the potential security threats and provide you with the advice and support to reduce that risk.
If you're checking for Merger & Acquisition (M&A) Risk, potential new partners or enhancing your understanding of your supply chain, ThreatLens® can support your objectives and provide near real-time viewpoints across organisations and the entire Internet.
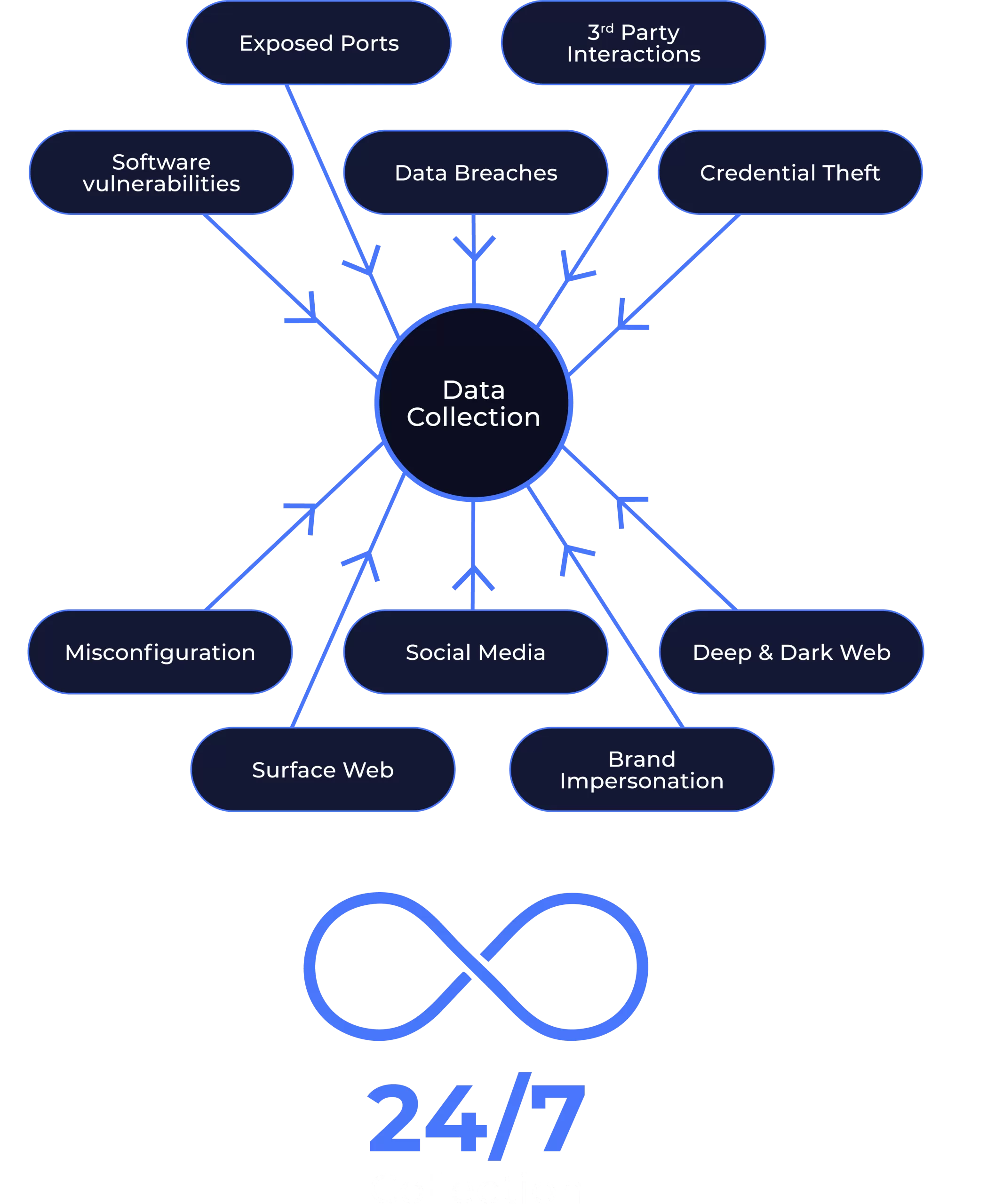
As ThreatLens® collects data, it enters our processing pipeline. This stage involves filtering the terabytes of raw data we collect every day. From exposed ports, software vulnerabilities, data breaches, supply chain risks and more. This process cuts through the noise to identify the risks that are most relevant to your organisation.
As ThreatLens® collects data, it enters our processing pipeline. This stage involves filtering the terabytes of raw data we collect every day. From exposed ports, software vulnerabilities, data breaches, supply chain risks and more. This process cuts through the noise to identify the risks that are most relevant to your organisation.

The analysis phase is arguably the most crucial. This is where human analysts verify the findings from ThreatLens®, correlate risks and mitigations and identify the key actions needed to protect your reputation. Removing the pain of sifting through false-positive alerts and instead providing high-fidelity insights to drive decision making and preventing cybercrime.
After the analysis phase, our analysts compile intelligence reporting bespoke to your situation and the risks you face. Giving you confidence whether in the boardroom or the security operations centre to drive change and make a positive impact on your companies reputation.
ADAPTED TO YOUR NEEDS
We also understand that you may not need every aspect of what ThreatLens® can do, and that's why we're delighted to offer an entirely modular approach to attack surface intelligence. Whether you only need data breach and credential theft monitoring, brand sentiment or our entire suite of services, we can adapt ThreatLens® to suit your needs.
THE THREE TIERS

THE STANDARD SERVICE
Dark Web Monitoring
Data Breaches and Credential Theft
Domain Monitoring
Brand Monitoring
External Vulnerability Scanning
Surface Web Monitoring
Monthly Consolidated Intelligence Report
THE ADVANCED SERVICE
Everything in Standard
VIP Monitoring
Phishing Kit Credential Theft Monitoring
Quarterly Threat Brief
Supply Chain & Partner Monitoring
Intelligence Requests for Information (RFIs)
Malware C2 Threat Feed for Proactive Blocking
Bespoke Requests
THE BESPOKE SERVICE
Pick and choose which features of ThreatLens® could support your business. No minimum service requirements.
Proactive cybersecurity starts with a conversation.
Contact us to fortify your digital footprint.
© 2025 Perspective Intelligence Perspective Intelligence® is registered in England and Wales under the company registration number 12903095. Registered Office Address: Eventus Sunderland Road, Market Deeping, Peterborough, PE6 8FD