Digital threats loom large in the world. External Attack Surface Intelligence (ASI) is a beacon of hope for organisations in it. They aim to safeguard their business from cybercrime. This process is vital. It includes finding, listing, sorting, and analysing all information on the internet about the organization. It also involves deciding what to focus on and keeping track of it. ASI focuses on the external attack surface. It shines a spotlight on sensitive data spread across the Internet. This helps to find and reduce vulnerabilities that cybercriminals can exploit.
As we navigate the nuances of attack surface intelligence, we will delve into identifying your external attack surface. We will also guide you on assessing risk and best practices for managing it. Defending your digital presence should focus on attack surface intelligence. It’s key for building cyber resilience. Understanding the outside attack surface is central to stopping cyber adversaries. So, it’s crucial for any organization’s proactive digital defense.
The Basics of External Attack Surface Intelligence
Diving into External Attack Surface Intelligence, it’s crucial to grasp the basics that underpin this vast collection of data and associated threat. Here’s a breakdown to guide you through:
-
Understanding the Landscape:
-
The Attack Surface Goes Beyond Your Network: Understanding that there will be data outside of your control is fundamental in appreciating the real risk of your attack surface. Beyond the systems and Internet-facing assets you have, is a wealth of data from social media, stolen credentials and news sites. While understanding software vulnerabilities and risks is important, it’s just one part of ASI in our opinion.
-
Stolen Credentials: This is possibly the biggest risk you may face if your organisation doesn’t utilise Multi-Factor Authentication (MFA) or allows bring your own device (BYOD). Credential theft and malware such as information-stealers can collect login credentials to internal systems on computers you have no visibility of, or control over.
- Key Elements of ASI:
-
- Systematic Approach: ASI is all about recognising, evaluating, and controlling vulnerabilities within your organisation’s digital infrastructure and beyond. It involves a careful process. It finds, analyses, and manages entry points that attackers might exploit. It focuses on external assets like internet-facing systems and services. Or, attackers might get in by buying stolen credentials from the dark web for as little as $10.
- Intelligence Analysis: After collecting and identifying all relevant data for an organisation, it is imperative that a human is able to analyse and contextualise the risk to the business. We use analytical methods to find and map the attack surface of your business. We also measure and manage it. The surface includes social media, the broader web, the company’s public assets, and the dark web. It’s a critical component of the whole process, providing a detailed overview of all points where an attacker could potentially infiltrate a system or extract data. We like to think of ASI as looking at the business through the eyes of a cybercriminal and looking for the same things they would gain any foothold that could result in a payday. Only we do this to provide the mitigation and protection so they won’t succeed.
- Capabilities and Outcomes:
- ASI Solutions: Key capabilities include dark web reconnaissance, continuous monitoring, and risk-based prioritisation, aimed at minimising attacks by external threat actors, whether through the patching of software vulnerabilities, ensuring employees affected by credential theft are notified and can take appropriate action, or by identifying accidental data exposures that could be leveraged to target the business.
- Benefits of ASI: Utilising Attack Surface Intelligence automates asset discovery and improves visibility, prioritising exposures for remediation as well as human-led intelligence collection and analysis using open-source intelligence (OSINT). It’s a solution that addresses challenges such as lack of visibility into external assets and inefficient remediation workflows, ultimately enhancing security controls when you either have a small team or need help in reducing your overall level of risk.
Attack Surface Intelligence is not just a tool. It’s a comprehensive approach. It includes continuous and automated management of cybersecurity risks. These risks are linked to an organisation’s external-facing digital assets. It includes monitoring, identifying, reducing, and mitigating risks across an organisation’s external attack surface. This surface includes known assets, unknown assets, rogue assets, and vendors. The platform provides unified external cyber defence. Intelligence drives this approach. It is key in today’s digital age. Understanding and securing one’s digital footprint is the way to reduce vulnerabilities. It lets you act before malicious actors exploit them.
Identifying Your External Attack Surface
Identifying your external attack surface is a critical step in safeguarding your organization from potential cyber threats. Here’s a structured approach to help you navigate this process effectively:
- Comprehensive Asset Identification:
- Technology Assets: Begin by cataloguing all technology assets including software applications, databases, websites, servers, and devices such as computers, phones, tablets, and even IoT devices. This foundational step ensures no asset is left unmonitored.
- Entry and Exit Points: Identify various points of entry and exit like UI forms and fields, HTTP headers and cookies, APIs, files, databases, and other local storage, including email or other message types, and runtime arguments. These points are potential gateways for cyber threats.
- Risk Assessment and Grouping:
- High-Risk Areas: Focus on remote entry points, interfaces with external systems, and areas allowing anonymous public access. These are typically high-risk areas needing immediate attention.
- Grouping by Function and Risk: Organise identified assets and entry/exit points into groups based on their function, design, technology, and associated risk levels. This categorisation aids in prioritizing security measures.
- Identifying Vulnerable Employees: Employees have a public profile or are in positions where they could be targeted (e.g. those who can pay invoices). They should consider having their digital footprint assessed for exposure of their work and personal accounts. When we conduct this kind of research, only the employee gets to see the report written for them, and we work with them to mitigate the findings so they can be better protected online.
- Utilising Tools and Controls:
- ASI Tools: Leverage tools like Spiderfoot for continuous discovery and mapping of your digital attack surface through its catalogue of API connections. Spiderfoot is an open-source tool. It offers an ‘outside-in’ perspective. It identifies, classifies, and then prioritises unknown and unmanaged internet-exposed resources. This enhances your view and control over your external attack surface.
- Implement Compensating Controls: Firewalls and intrusion detection systems reduce risks. These controls help protect assets and entry points.
By methodically identifying and sorting your external attack surface, you gain better visibility into your organisation’s digital footprint. You also empower your cybersecurity team to prioritize and fix vulnerabilities before attackers exploit them.
Assessing and Measuring Your External Attack Surface
Assessing and measuring your external attack surface is paramount in understanding and mitigating the risks associated with your digital assets. Here’s a structured approach to guide you through this critical process:
1.Comprehensive Analysis and Continuous Monitoring
- Automated Discovery and Mapping: As mentioned above, doing regular scans to find and map assets in your IT estate is key. External research and analysis are also crucial. They let you understand the risk to your business from the outside.
- Continuous Monitoring: Implement solutions that provide real-time monitoring of your external attack surface. This enables the timely detection of new risks and vulnerabilities as they emerge, ensuring that your security posture is always up-to-date. ASI clients at Perspective Intelligence get access to our online portal, powered by Dark Invader to assist with this for both their domains, and for VIP monitoring.
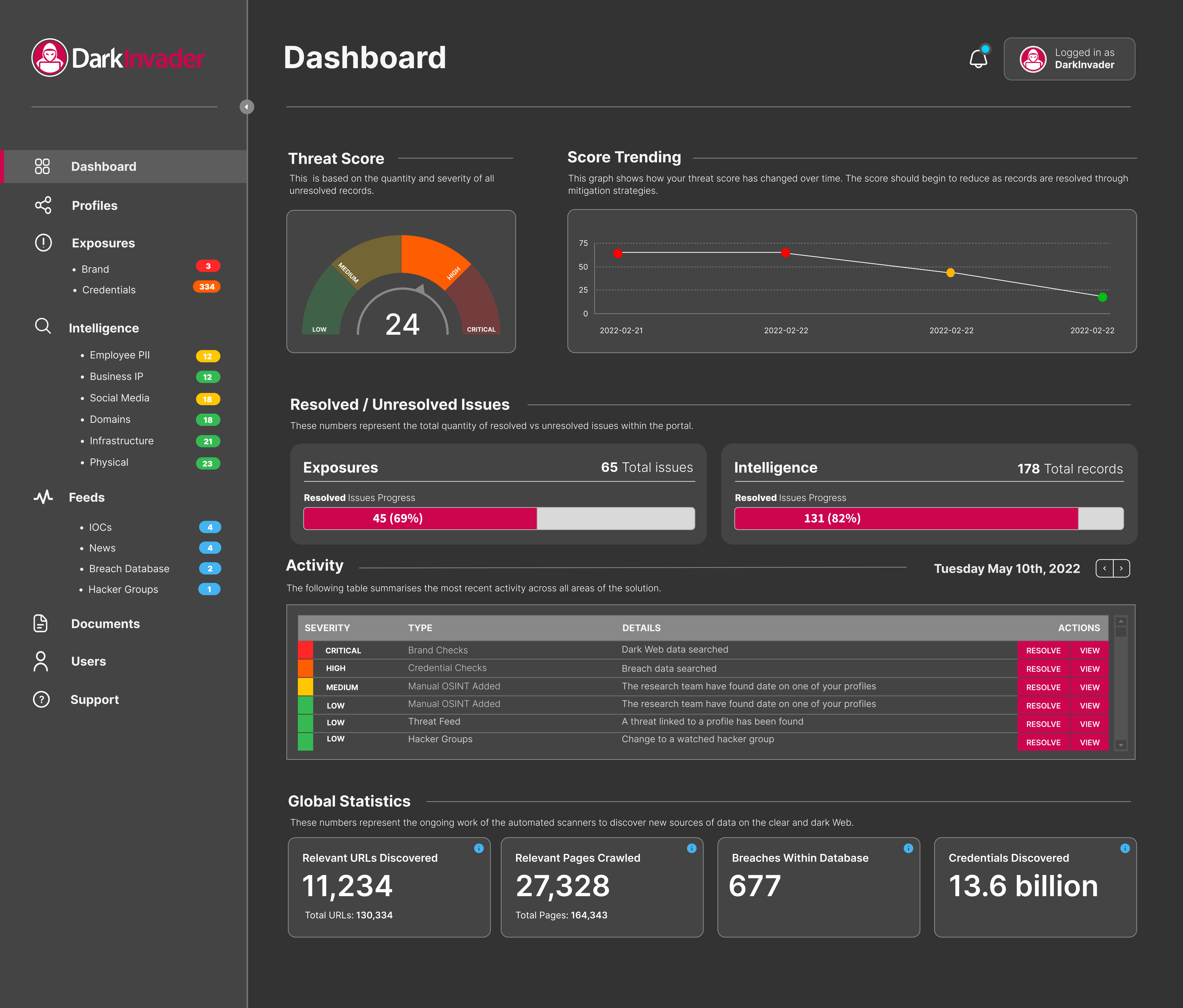
2.Vulnerability Identification and Risk Prioritisation
- Vulnerability Scanning and Penetration Testing: Do them regularly. They find and show the risks in your external-facing assets. This insight is crucial for prioritizing security efforts effectively. Through our online portal you can run regular vulnerability scans across your domains to identify potential risks.
- Multi-layered Prioritisation Approach: Adopt a multi-layered approach to prioritising risks. Consider factors such as severity scores, exploitability, and the potential impact (blast radius) of each vulnerability. This method ensures that the most critical issues are addressed first, optimising your security resources. Understanding what systems may be affected by the latest big news flaw will be easily achieved when you understand what your Internet-facing assets look like.
3.Mitigation and Remediation Workflow Integration
- Actionable Mitigation Plans: Develop and provide actionable plans for mitigating the prioritised threats. This includes specific steps and measures that can be taken to address each identified risk. ASI clients of Perspective Intelligence receive a mitigation plan as part of their service when we provide in-depth ASI reports.
- Integration with Security Tools and Processes: Ensure that your remediation workflow is seamlessly integrated with existing security tools and processes. This facilitates efficient and effective mitigation of vulnerabilities, enhancing your overall security posture.
- Empower Employees: Your business should adopt technologies like Password Managers and MFA. These steps go a long way to stopping cybercriminals. By raising the barrier to entry for your business, you force the criminals to move to easier targets, safeguarding your data and protecting your customers.
By using a structured approach to assess your attack surface, you can see your digital footprint well. You can find weaknesses in your external assets and keep checking your security posture. This proactive stance not only identifies misconfigurations and insecure practices but also enables timely detection and response to emerging threats, optimizing IT and security costs while streamlining operations.
Best Practices for Managing Your External Attack Surface
To effectively manage your external attack surface, embracing a blend of technology, strategy, and proactive measures is paramount. Here’s a breakdown to guide you:
- Leverage Comprehensive ASI Tools:
- Inventory and Mapping: Ensure the tool provides a complete inventory of all external-facing assets and a detailed attack surface map, highlighting potential attack paths and their blast radius.
- Security Exposures and Prioritization: It should offer a comprehensive view of security exposures and a prioritised list of vulnerabilities, enabling focused remediation efforts.
- Comprehensive Dark Web Coverage: In addition to understanding the risk from brand impersonation, “typosquat” (e.g. copycat) web domains and brand infringement, you also need comprehensive coverage of your business across the deep and dark web. A thorough ASI report will give you the whole picture of your business’ attack surface at the time of the report, don’t settle for anything less.
- Adopt Proactive ASI Strategies:
- Integration of Threat Intelligence: Utilise cyber threat intelligence (CTI) for proactive risk mitigation and stay ahead of potential threats.
- Regular Assessments: Employ penetration testing and red teaming, alongside ongoing surveillance and frequent vulnerability scans, to uncover and address vulnerabilities.
- Vendor Selection: When choosing ASI vendors, consider their expertise, tool comprehensiveness and accuracy, solution scalability, and customer support level.
- Implement Protective Measures and Training:
- Protective Controls: Install antivirus software, application firewalls, password managers, MFA and endpoint encryption to safeguard against attacks.
- Security Awareness Training: Ensure your security roadmap includes training programs focusing on likely attack vectors to educate employees on best practices and threat awareness.
- Policy Enforcement and Compliance: Enforce security policies and procedures to regulate how employees manage enterprise data and access resources. Additionally, ensure your program meets regulatory compliance requirements for a holistic security posture.
By incorporating these practices, your organisation can not only detect and mitigate vulnerabilities more effectively but also enhance its overall security posture. This proactive approach to managing the external attack surface ensures that assets are continuously monitored, vulnerabilities are promptly addressed, and you remain resilient against evolving cyber threats.
Conclusion
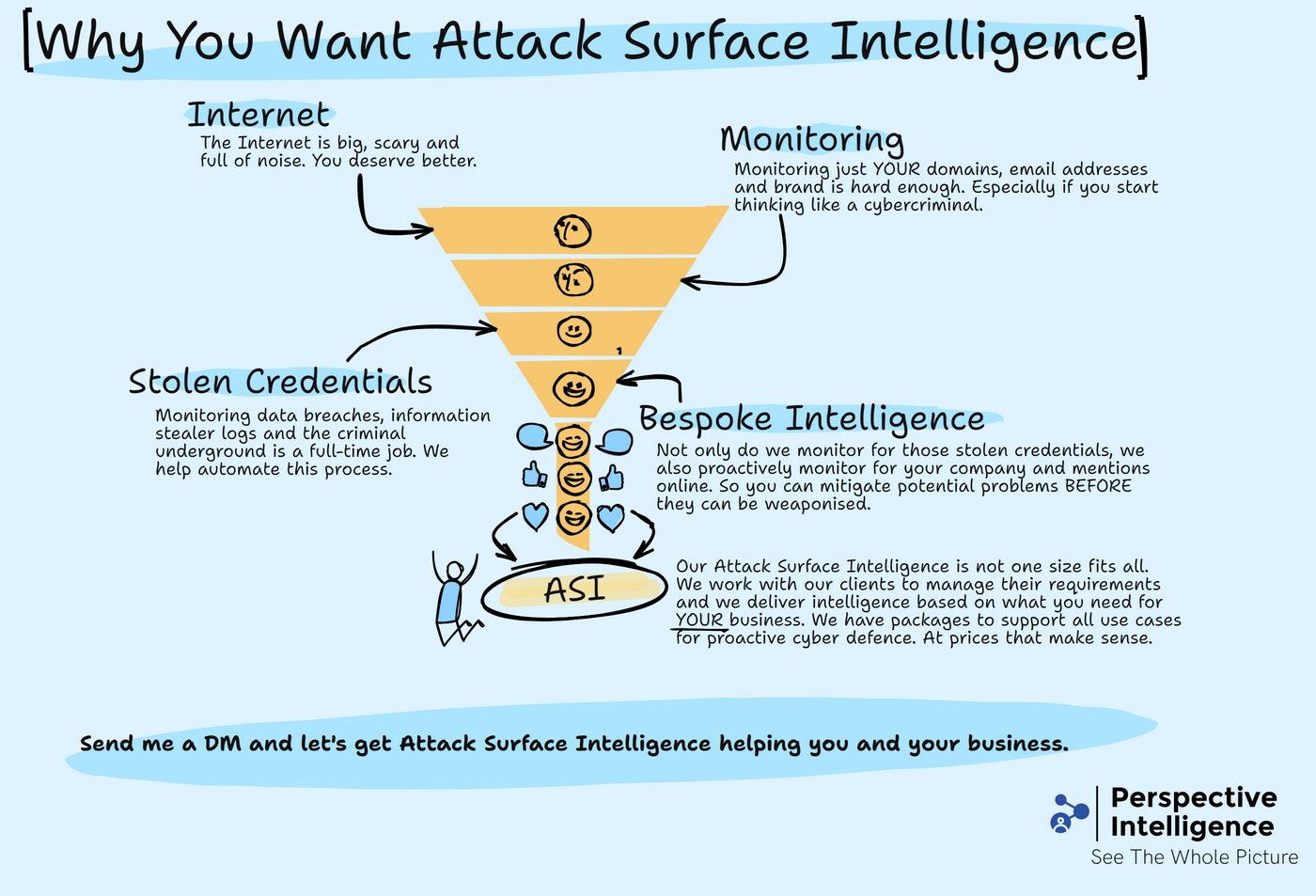
An image we shared on social media recently conveying the funnel of Attack Surface Intelligence
Through this exploration, we have delved into the complex world of Attack Surface Intelligence. It has a critical role in making organisational cybersecurity stronger. We’ve examined how identifying, assessing, and managing the external attack surface empowers you to proactively mitigate vulnerabilities, thereby enhancing resilience against cyber threats. By leveraging advanced tools and adopting a systematic approach towards continuous monitoring and threat intelligence integration, you can significantly reduce your exposure to external threats. This narrative underscores the indispensable nature of ASI in today’s digital landscape, where cyber threats are ever-evolving and the need for comprehensive cyber defence mechanisms are paramount.
The journey through the facets of ASI, from identification and assessment to best practices in management, illuminates a path towards achieving a more secure digital footprint. In essence, the effective management of the external attack surface is not merely a technical requirement but a strategic imperative for all organisations aiming to safeguard their digital assets against potential cyber adversities. As we conclude, let this serve as a reminder of the importance of adopting an intelligence-led approach to cyber defence, echoing the expertise and insights of organidations such as Perspective Intelligence, which stand at the forefront of empowering businesses with the tools and knowledge to navigate the complexities of cyber threats proficiently. We believe a human-led approach is necessary to underscore the significance of tailored cyber intelligence strategies in enhancing organisational security postures, now and into the future.
FAQs
What is the definition of an external attack surface?
An external attack surface refers to the process of detecting and managing assets within a business that are exposed to the public internet. This includes the task of tracking vulnerabilities, misconfigurations in public clouds, exposed credentials, and other external data and processes that could potentially be exploited by attackers.
How does attack surface intelligence benefit an organisation?
Attack Surface Intelligence aids organisations in significantly reducing risks by enhancing the visibility of assets, prioritising the remediation of exposures, and implementing effective security controls.
Can you outline the process involved in analysing an attack surface?
The analysis of an attack surface involves several key steps: identifying potential entry points and vulnerabilities that could be targeted, evaluating the effectiveness of current security measures in place, and assessing the potential consequences of a successful attack.
What are the different categories of attack surfaces?
Experts in security categorise attack surfaces into three main types: the digital, the physical, and the social engineering attack surfaces. Each represents a different aspect of an organisation’s vulnerability to potential attacks.
About Perspective Intelligence
Perspective Intelligence is a United Kingdom-based cyber intelligence specialist. We offer services across attack surface, cyber threat and open-source intelligence in addition to intelligence training services both in-person and online.
About Aaron Roberts
Aaron Roberts is an intelligence professional specialising in Cyber Threat Intelligence (CTI) and Open-Source Intelligence (OSINT). He is focused on building intelligence-led cyber capabilities in businesses of all sizes and conducting online investigations and research. He has worked within the public and private sectors and the British Military. As such, he understands how intelligence can and should be utilised within all environments and the fundamental approach businesses must take to get the maximum value out of their cyber intelligence program.
Aaron founded Perspective Intelligence in 2020 as he identified several ways in which his experience could support and improve the underlying security posture of organisations across the UK and globally. Aaron delivers training on behalf of Perspective Intelligence and is the author of the book Cyber Threat Intelligence: The No-Nonsense Guide for CISOs and Security Managers.